DPBuddy 3.5 supports in-depth inventory and analysis of your X.509 certificates and keys:
-
Inventory of all your certificates, keys and password aliases across all of your appliances and domains.
In addition to DataPower, the inventory includes certificates from TLS endpoints. - Reports in Excel and text format
- Certificate deduplication — find all places where a given certificate is used
- See audit records of all changes — who changed what when
- See how each of your crypto objects is used by other DataPower objects
- See expiration for passwords/password aliases (in addition to certificates’ expiration)
- Ensure compliance and best practices: identify self-signed certificates, weak keys/algorithms, unapproved signers
- Get alerted on certificate expiration, invalid signatures, revocation, policy violations
Here are examples of various reports generated by the “listCrypto” command.
Certificates with their audit records. You can see that the same cert (lines 2-5) is deployed multiple times under different file names.
The cert at line 5 was downloaded directly from the endpoint.
Domain Object Name File Subject CN Alt Names Exp in Days Key Alg Issuer Serial Changed On Changed By dpbuddy-samples revoked_chain cert:/revoked_chain.pem revoked.badssl.com revoked.badssl.com,www.revoked.bads 473 RSA-2048 DigiCert SHA2 Secure Server CA 4578095623763233818958520798617405692 6/20/20 aananiev dpbuddy-samples myarch_chain cert:/myarch_chain.pem myarch.com myarch.com,www.myarch.com 493 RSA-2048 Go Daddy Secure Certificate Authori 11510493113533735686 6/20/20 aananiev dpbuddy-samples myarch cert:/myarch.pem myarch.com myarch.com,www.myarch.com 493 RSA-2048 Go Daddy Secure Certificate Authori 11510493113533735686 6/20/20 aananiev dpbuddy-samples myarch.com_443 cert:/myarch.com_443.pem myarch.com myarch.com,www.myarch.com 493 RSA-2048 Go Daddy Secure Certificate Authori 11510493113533735686 6/20/20 aananiev https://myarch.com:443 myarch.com myarch.com,www.myarch.com 493 RSA-2048 Go Daddy Secure Certificate Authori 11510493113533735686 dpbuddy-samples local-app cert:/local-app.pem local-app local-app 326 RSA-2048 Local CA 1589417790 6/20/20 aananiev dpbuddy-samples local_app cert:/local_app.pem local-app.com 266 RSA-2048 local CA 1584288750 6/20/20 aananiev dpbuddy-samples self_signed cert:/self_signed.pem localhost -523 RSA-2048 localhost 9699314724490867386 6/20/20 aananiev dpbuddy-samples keypair-1 cert:/keypair-1.pem test-key-1 -278 RSA-2048 test-key-1 1537189500 6/20/20 aananiev
Results of the certificate compliance verification; reported in the “Problems” column
Object Name File Subject CN Exp in Days Key Alg Issuer Serial Changed On Changed By Problems revoked_chain cert:/revoked_chain.pem revoked.badssl.com 473 RSA-2048 DigiCert SHA2 Secure Server CA 4578095623763233818958520798617405692 6/20/20 aananiev Duration exceeds,Ocsp revoked myarch_chain cert:/myarch_chain.pem myarch.com 493 RSA-2048 Go Daddy Secure Certificate Authori 11510493113533735686 6/20/20 aananiev Duration exceeds,Blacklisted issuer myarch cert:/myarch.pem myarch.com 493 RSA-2048 Go Daddy Secure Certificate Authori 11510493113533735686 6/20/20 aananiev Duration exceeds,Blacklisted issuer myarch.com_443 cert:/myarch.com_443.pem myarch.com 493 RSA-2048 Go Daddy Secure Certificate Authori 11510493113533735686 6/20/20 aananiev Duration exceeds,Blacklisted issuer local-app cert:/local-app.pem local-app 326 RSA-2048 Local CA 1589417790 6/20/20 aananiev local_app cert:/local_app.pem local-app.com 266 RSA-2048 local CA 1584288750 6/20/20 aananiev self_signed cert:/self_signed.pem localhost -523 RSA-2048 localhost 9699314724490867386 6/20/20 aananiev Expired,Self signed keypair-1 cert:/keypair-1.pem test-key-1 -278 RSA-2048 test-key-1 1537189500 6/20/20 aananiev Expired,Self signed
Certificate checks are configured in “crypto.conf” as following:
expiration: {
days: 30
}
duration: {
days: 365
}
selfSigned: {
allow: false
}
sigVerification: {
failIfNoIssuer: false
}
ocsp: {
enabled: true
}
pubKey: {
minSize: {RSA: 2048, EC: 256}
allowedAlgs: [RSA, EC]
}
Private keys with usages:
Object Name File Usage dp-myarch-key cert:/dp_myarch.key CryptoIdentCred:dp-myarch-cred datapower.myarch.com_privkey cert:/datapower.myarch.com_privkey.pem local-app_privkey cert:/local-app_privkey.pem local-app-ss_privkey cert:/local-app-ss_privkey.pem CryptoIdentCred:datapower-local-ca, SSLServerProfile:dp-myarch-server, XMLFirewallService:OktaResourceOwnerFlow sslserver cert:/sslserver-privkey.pem CryptoIdentCred:sslserver, CryptoProfile:sslserver, SSLProxyProfile:sslserver, HTTPSSourceProtocolHandler:https_5041, MultiProtocolGateway:oauth-mpgw-rs
Password aliases with expiration and usages:
Location Domain Object Name Exp in Days Changed On Changed By Usage dev dpbuddy-samples self_signed_key-pwd 6/20/20 aananiev CryptoKey:self_signed_key dev dpbuddy-samples oracle-pwd-alias 83 3/16/20 aananiev dev dpbuddy-samples keypair-1_key-pwd 6/20/20 aananiev CryptoKey:keypair-1_key dev dpbuddy-samples service1-pwd-alias -66 3/16/20 aananiev dev dpbuddy-samples service2-pwd-alias -97 3/16/20 aananiev
The report in Excel format provides additional information, here is the snippet of the report:
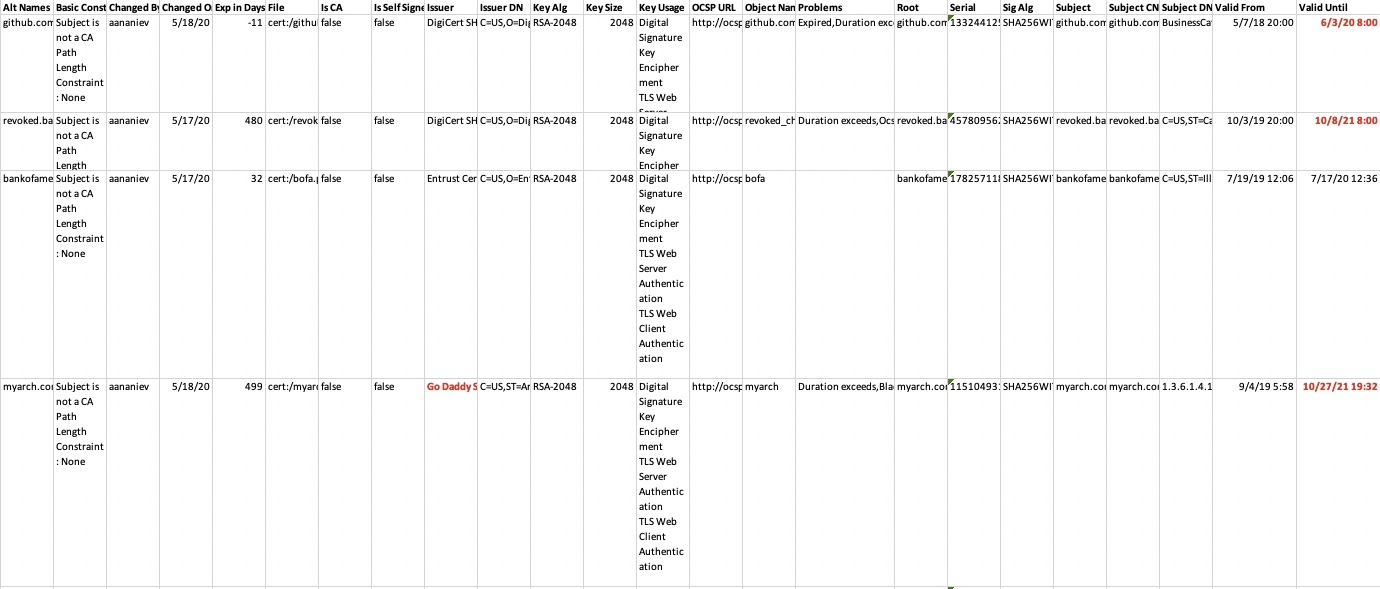
More details are available in the documentation.
If you’re interested in fully automating your certificate and key management, please let us know.
